Back in the good old pre-COVID days, I loved to attend every single IT conference or event I could in person, and the swag you’d get was always super cool – including those very nice USB memory sticks with promotional materials or catalogs. The thing is, most of us would just plug those in without a second thought and browse content willy-nilly… who doesn’t love free stuff?
The huge problem is, any of those cool USB sticks could’ve been the ultimate trojan horse from hell in the form of a tool known in the information security world as a Rubber Ducky, and you pretty much opened your home front door, offered a beer, invited them to sleep with your spouse and cooked them breakfast the next morning!
Ok Marco you got my attention… so what is a Rubber Ducky attack?
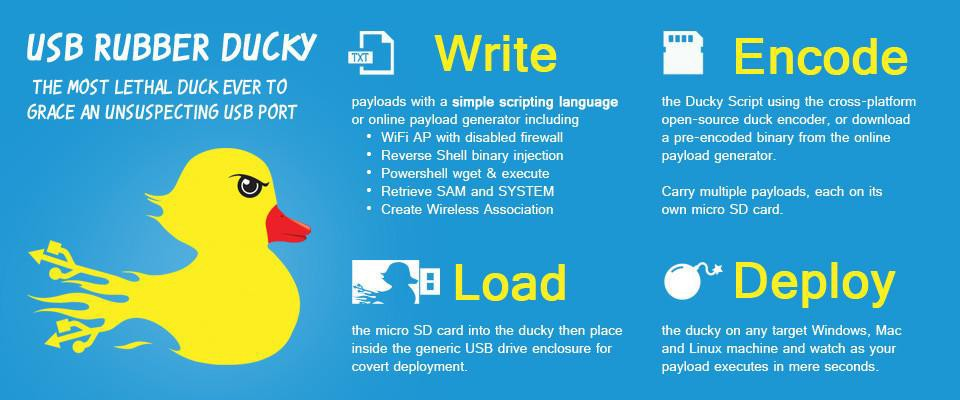
According to Team Ascend, “The Rubber Ducky hacking tool [created by an information security company called Hak5 in 2205], along with similar tools that have emerged after it, gave criminals an easy way to take the ease and portability of a “flash drive” and use it to hack. The Rubber Ducky uses keystroke injection technology to run malicious code quickly and easily on a device—serving as an unsuspecting way to steal passwords, drop malware, install “backdoors” into systems, exfiltrate data, and more”.
Here’s how a Rubber Ducky looks like:
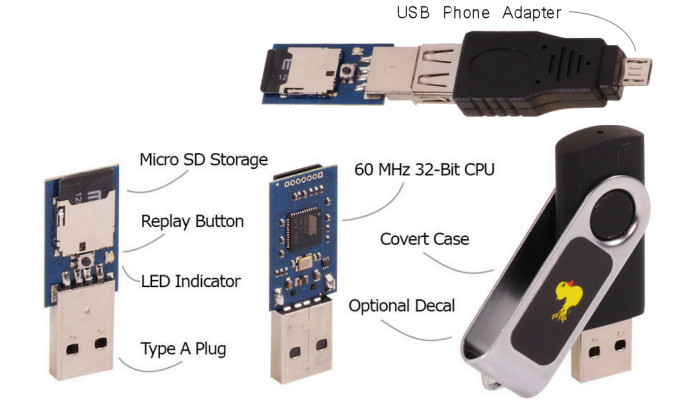
Photo: https://bit.ly/3eml1Su
What happens when you plug that infernal device in?
The USB device has a minicomputer that starts running code saved in the tiny micro-SD, and this happens in few seconds! Some attacks are “blink and you miss it”, others are so sophisticated that you won’t see anything on the screen. It will then grant complete access to the attacked/compromised system by “phoning home” to a command-and-control centre and at this point is pretty much game over.
Although Rubber Duckies are often used by hackers to get access to corporate networks (a common tactic is to drop a bunch of those USB sticks around the target organization hoping somebody would pick one up and just plug it in their work computer), it is also a valuable tool used by penetration testers and security professionals known as red teamers. These individuals are often hired by businesses to test their networks and they have explicit authorization to use any tool necessary to compromise a network.
How to protect yourself against a Rubber Ducky attack?
If you work for a large organization, it is highly likely their IT department has some sort of endpoint/intrusion detection technologies that could potentially stop the attack. Still, you should not be plugging USB sticks you find lying on the street in your work PC.
If you are an individual, the only protection you have is this: do not plug in any USB stick you do not fully trust its source!
Black hat hackers (the naughty ones) are very, very smart individuals – sometimes organizations – and we are often one or two steps behind. I always say that anybody and everything can be hacked, if the intention, motivation, and resources are there – just don’t make it too easy for the bad guys to get you!






